Source article
The following script automates the process and works across all Linux distros because it has no dependencies on specialized packages. It simply parses the output of the ip command, isolates the vendor part of mac address into a variable which is finally grep‘ed through an online DB of vendor prefixes.
#!/bin/bash
OUI=$(ip addr list|grep -w 'link'|awk '{print $2}'|grep -P '^(?!00:00:00)'| grep -P '^(?!fe80)' | tr -d ':' | head -c 6)
curl -sS "http://standards-oui.ieee.org/oui.txt" | grep -i "$OUI" | cut -d')' -f2 | tr -d '\t'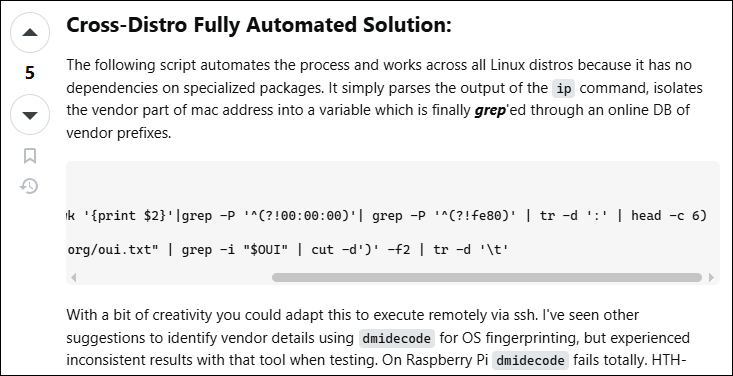
Querying the IEEE OUI Database
curl -sS "http://standards-oui.ieee.org/oui.txt" | grep -i "$OUI" | cut -d')' -f2 | tr -d '\t'curl -sS "http://standards-oui.ieee.org/oui.txt":
- Fetches the official IEEE OUI database, which contains MAC-to-vendor mappings.
- The
-sSoptions suppress progress output and errors.
grep -i "$OUI":
- Searches for the extracted OUI in the IEEE OUI database.
- The
-iflag makes the search case-insensitive.
cut -d')' -f2:
- Extracts the text after the closing parenthesis
), which contains the vendor name.
tr -d '\t':
- Removes any tab characters for cleaner output.
Instead of “ip a list” use “arp“
Here is the adapted Bash script that extracts the OUI from the MAC address appearing in the third column of the arp command output and then retrieves the manufacturer information from the IEEE OUI database.
#!/bin/bash
# Extract OUI from the third column of the arp command output
OUI=$(arp -a | awk '{print $3}' | grep -P '^(?!00:00:00)' | grep -P '^(?!fe80)' | tr -d ':' | head -c 6)
# Fetch OUI manufacturer details
curl -sS "http://standards-oui.ieee.org/oui.txt" | grep -i "$OUI" | cut -d')' -f2 | tr -d '\t'Explanation of Changes
- Using
arp -a- Extracts ARP table entries which contain MAC addresses.
- Extracting the MAC Address (3rd column)
awk '{print $3}': Selects the third column where MAC addresses appear.grep -P '^(?!00:00:00)': Ensures invalid MACs (like00:00:00:...) are excluded.grep -P '^(?!fe80)': Ensures no link-local IPv6 addresses are included.tr -d ':': Removes colons from the MAC address.head -c 6: Extracts the first 6 characters (OUI).
- Querying the IEEE OUI Database
- The script then fetches the manufacturer information as before.
MAC of a AudioCodes MP-118 FXS
00:90:8f:a3:9b:d1MAC of a Yealink phone
24:9a:d8:62:19:07MAC of a Polycom phone
00:04:f2:2e:a4:81MAC of a Cisco phone
00:19:e7:10:dc:8eMAC of a Hewlett Packard PC
24:6a:0e:82:4c:f4MAC of a Dell PC
78:2b:cb:8c:cb:deNode.js project
Overview
This code sets up a simple web server using Express.js that provides an API endpoint to look up the manufacturer of a network device based on its MAC address. It uses an OUI (Organizationally Unique Identifier) database to perform this lookup. The OUI is the first 6 characters of a MAC address and identifies the manufacturer.
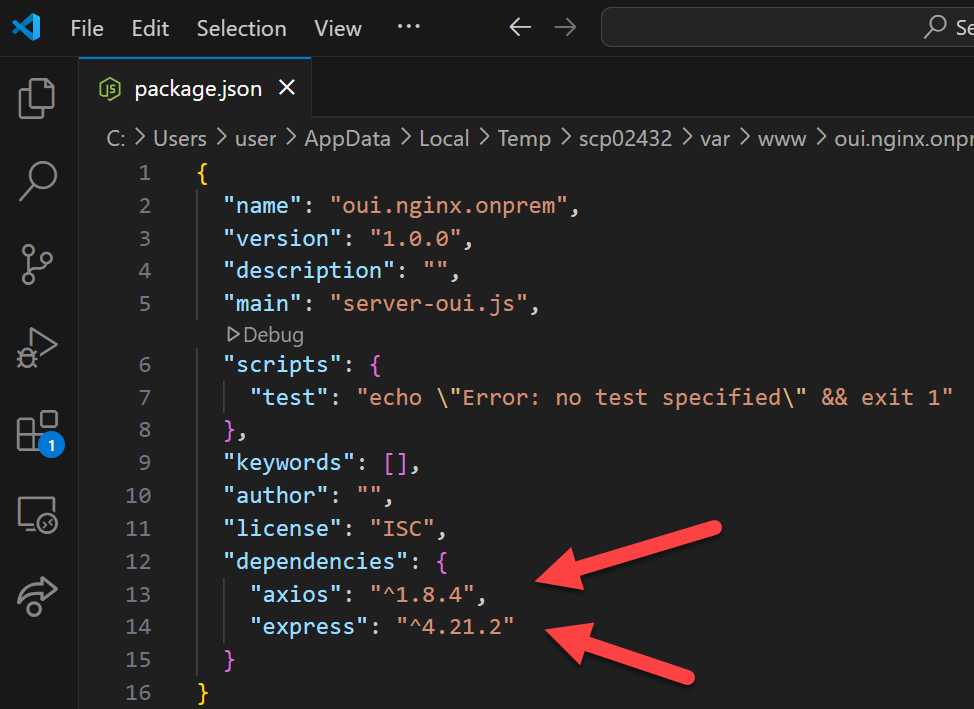
Install dependencies with npm
npm install express axiosaxios: Imports the Axios library, which is used to make HTTP requests to fetch the OUI database from the specified URL.express: Imports the Express.js framework, which is used to create the web server and define API endpoints.
Node.js backend test
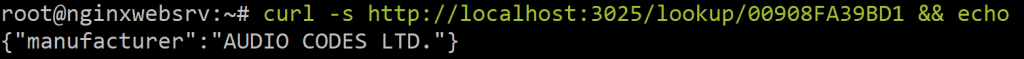
Test with CURL command
curl -s http://localhost:3025/lookup/00908FA39BD1 && echoPrevent API abuse
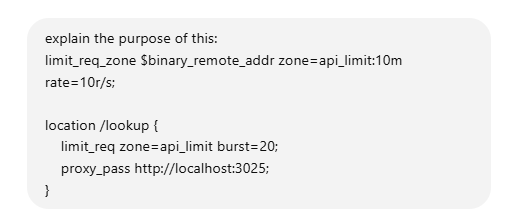
This Nginx configuration is implementing rate limiting for requests to the /lookup endpoint. Here’s a breakdown of what each directive does:
1. Nginx main config file
etc > nginx > nginx.conf
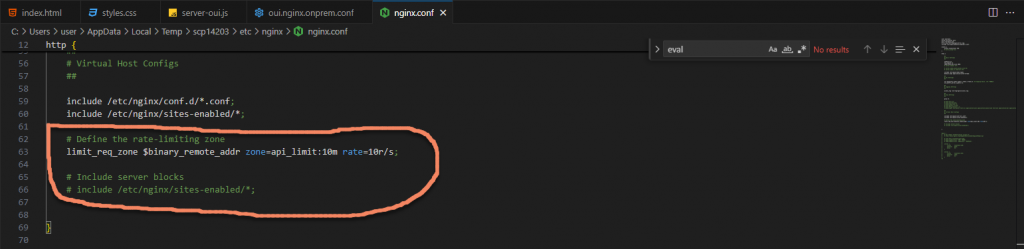
vim /etc/nginx/nginx.conf# Define the rate-limiting zone
limit_req_zone $binary_remote_addr zone=api_limit:10m rate=10r/s;
# Include server blocks
# include /etc/nginx/sites-enabled/*;limit_req_zonedefines a shared memory zone (api_limit) to track request rates.$binary_remote_addruses the binary representation of the client’s IP address to uniquely identify them.zone=api_limit:10mcreates a memory zone of 10MB, which can store around 160,000 unique IP addresses.rate=10r/slimits each IP to 10 requests per second.
2. Server Block config file
etc > nginx > sites-available
vim /etc/nginx/sites-available/oui.nginx.onprem.conf# Rate limiting for /lookup endpoint
location /lookup {
limit_req zone=api_limit burst=20 nodelay; # Apply rate limiting
proxy_pass http://localhost:3025;
}- Applies rate limiting to
/lookuprequests. limit_req zone=api_limit burst=20;- Uses the
api_limitzone for rate limiting. - Allows temporary bursts of up to 20 requests beyond the 10 requests/second limit.
- Excess requests are delayed rather than dropped (unless the queue exceeds 20).
- Uses the
proxy_pass http://localhost:3025;- Forwards requests to the backend server running on port 3025.
Nginx Server Block file
etc > nginx > sites-available
server {
root /var/www/oui.ciscoar.com;
index index.html;
server_name oui.ciscoar.com www.oui.ciscoar.com;
# Main location block
location / {
proxy_pass http://localhost:3025;
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_cache_bypass $http_upgrade;
# Timeout settings
proxy_connect_timeout 60s;
proxy_send_timeout 60s;
proxy_read_timeout 60s;
}
# Rate limiting for /mac-lookup endpoint
location /lookup {
limit_req zone=api_limit burst=20 nodelay; # Apply rate limiting
proxy_pass http://localhost:3025;
}
listen 443 ssl; # managed by Certbot
ssl_certificate /etc/letsencrypt/live/oui.ciscoar.com/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/oui.ciscoar.com/privkey.pem; # managed by Certbot
include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
# SSL Best Practices
#ssl_protocols TLSv1.2 TLSv1.3; # Disable older protocols like TLSv1.0 and TLSv1.1
#ssl_ciphers HIGH:!aNULL:!MD5; # Use strong ciphers
#ssl_prefer_server_ciphers on; # Prefer server's cipher order
#ssl_session_cache shared:SSL:10m; # Enable session caching for performance
#ssl_session_timeout 10m; # Session timeout
# Security headers
add_header X-Frame-Options "SAMEORIGIN" always;
add_header X-Content-Type-Options "nosniff" always;
add_header Referrer-Policy "strict-origin" always;
add_header Strict-Transport-Security "max-age=31536000; includeSubDomains" always; # Enable HSTS
}
server {
if ($host = www.oui.ciscoar.com) {
return 301 https://$host$request_uri;
} # managed by Certbot
if ($host = oui.ciscoar.com) {
return 301 https://$host$request_uri;
} # managed by Certbot
listen 80;
server_name oui.ciscoar.com www.oui.ciscoar.com;
return 404; # managed by Certbot
}Node.js Server JavaScript file
http://standards-oui.ieee.org/oui.txt
const express = require("express");
const axios = require("axios");
const app = express();
const PORT = 3025;
// OUI Database URL
const OUI_URL = "http://standards-oui.ieee.org/oui.txt";
// Cache to store OUI data after first fetch
let ouiData = null;
// Function to fetch and parse the OUI database
async function getManufacturer(oui) {
try {
// Fetch OUI data if not already loaded
if (!ouiData) {
// console.log("Fetching OUI data...");
try {
const response = await axios.get(OUI_URL);
ouiData = response.data.split("\n");
} catch (fetchError) {
console.error("Failed to fetch OUI data:", fetchError.message);
throw fetchError; // Re-throw the error for the caller to handle
}
}
// Search for the OUI in ouiData
// console.log(`Searching for OUI: ${oui}`);
const result = ouiData.find(line => line.toUpperCase().includes(oui.toUpperCase()));
// console.log(`Mac Lookup result: ${result}`);
return result ? result.split(")")[1].trim() : "Unknown Manufacturer";
} catch (error) {
// Handle other errors (e.g., parsing or unexpected issues)
// console.error("Error in getManufacturer:", error.message);
return "Unknown Manufacturer"; // Fallback value
}
}
// API endpoint for OUI MAC Lookup
app.get("/lookup/:mac", async (req, res) => {
let mac = req.params.mac.toUpperCase().replace(/[^0-9A-F]/g, ""); // Remove non-hex characters
if (mac.length !== 12) {
return res.json({ error: "Invalid MAC format" });
}
const oui = mac.substring(0, 6); // Extract first 6 characters
const manufacturer = await getManufacturer(oui);
res.json({ manufacturer });
});
// Serve static HTML page
app.use(express.static(__dirname));
app.listen(PORT, () => console.log(`Server running at http://localhost:${PORT}`));Purpose of This Configuration
- Prevents API abuse – Stops a single client from overwhelming the
/lookupendpoint with too many requests. - Allows short bursts – If a client temporarily exceeds the limit, up to 20 extra requests can queue instead of being immediately rejected.
- Protects the backend – Limits the load on the Express.js server, preventing high traffic from slowing it down.
Example Behavior
- If a user sends 10 requests per second, all are processed normally.
- If a user suddenly sends 15 requests per second, 10 are processed immediately, and 5 are queued (delayed but not rejected).
- More than 30 requests in one second, the extra requests are dropped.
This is a good way to prevent DoS (Denial of Service) attacks and ensure fair API usage.